%20CEH%20Course%20?unique=2a06b8b)
Certified Ethical Hacker v13 (AI) CEH Course
| Responsible | Techventurz |
|---|---|
| Last Update | 08/04/2025 |
| Members | 2 |
%20CEH%20Course?unique=d63ed66)
Prerequisites for Certified Ethical Hacker v13 (AI) CEH Course
To ensure you have the best learning experience in our Certified Ethical Hacker v13 (AI) course, it's recommended that you meet the following minimum prerequisites:
- Basic Networking Knowledge: Understanding of basic networking concepts and protocols such as TCP/IP, DNS, and OSI model.
- Fundamental Cybersecurity Concepts: Familiarity with basic cybersecurity principles and practices, including understanding of common threats and vulnerabilities.
- Experience with Operating Systems: Practical experience with different operating systems, particularly Windows and Linux, as you'll need to navigate and perform tasks in these environments.
- Basic Knowledge of Programming: Some understanding of programming or scripting languages can be beneficial but is not mandatory.
- Prior IT Experience: Having 1-2 years of experience in IT, particularly in network support, systems administration, or security roles, will be advantageous.
While these prerequisites help, they are not strict requirements. Enthusiasm and a willingness to learn can also pave the way for your success in this course. If you are passionate about cybersecurity and ethical hacking, our comprehensive training will equip you with the skills and knowledge you need.
RoadMaps
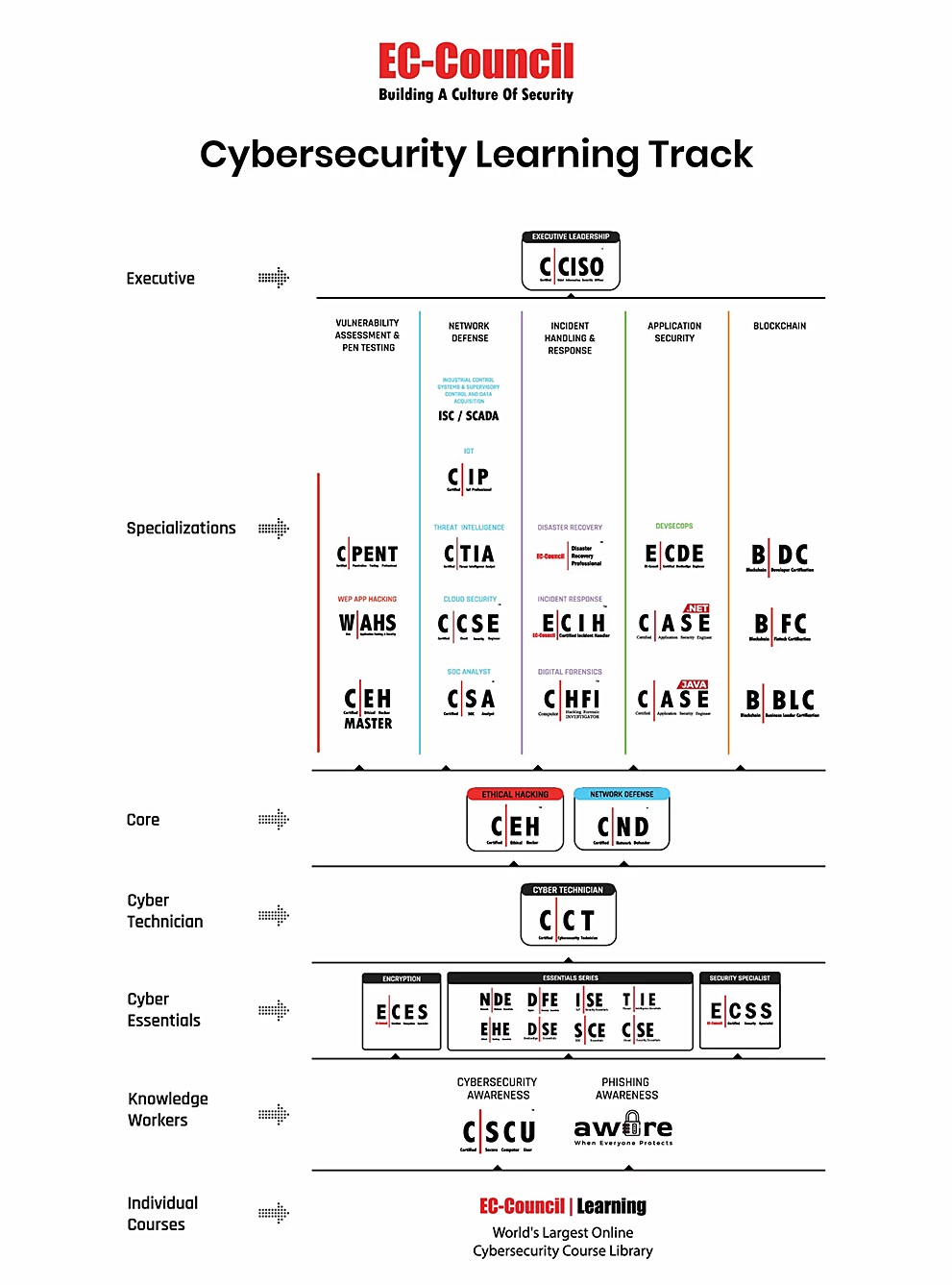
Target Audience for Certified Ethical Hacker v13 (AI) CEH
Certified Ethical Hacker v13 (CEH) offers advanced training in ethical hacking powered by AI capabilities, targeting IT professionals aiming to enhance their cybersecurity skills.
- Ethical Hackers
- Penetration Testers
- Network Security Specialists
- Information Security Analysts
- Cybersecurity Consultants
- IT Auditors
- Site Administrators
- System Administrators
- IT Managers
- Aspiring Cybersecurity Professionals
Learning Objectives - What you will Learn in this Certified Ethical Hacker v13 (AI) CEH?
Certified Ethical Hacker (CEH) v13 Course Introduction
The Certified Ethical Hacker (CEH) v13 course equips students with the essential skills to identify, counter, and prevent cyber threats using the latest AI-powered techniques and tools. The training encompasses a wide array of security domains, from social engineering to cloud computing.
Learning Objectives and Outcomes
- Introduction to Ethical Hacking: Understand the fundamentals of ethical hacking, information security controls, relevant laws, and standard procedures.
- Footprinting and Reconnaissance: Learn techniques and tools for gathering information during the pre-attack phase.
- Scanning Networks: Master network scanning techniques and countermeasures.
- Enumeration: Discover various techniques including BGP and NFS exploits, and identify countermeasures.
- Vulnerability Analysis: Identify security loopholes and learn about different vulnerability assessment tools and types.
- System Hacking: Explore methodologies like steganography and steganalysis for identifying system and network vulnerabilities.
- Malware Threats: Understand different types of malware, procedures for malware analysis, and countermeasures.
- Social Engineering: Learn techniques for identifying theft attempts and auditing human-level vulnerabilities.
- **Denial-of-Service (DoS
%20CEH%20Course?unique=d63ed66)
Prerequisites for Certified Ethical Hacker v13 (AI) CEH Course
To ensure you have the best learning experience in our Certified Ethical Hacker v13 (AI) course, it's recommended that you meet the following minimum prerequisites:
- Basic Networking Knowledge: Understanding of basic networking concepts and protocols such as TCP/IP, DNS, and OSI model.
- Fundamental Cybersecurity Concepts: Familiarity with basic cybersecurity principles and practices, including understanding of common threats and vulnerabilities.
- Experience with Operating Systems: Practical experience with different operating systems, particularly Windows and Linux, as you'll need to navigate and perform tasks in these environments.
- Basic Knowledge of Programming: Some understanding of programming or scripting languages can be beneficial but is not mandatory.
- Prior IT Experience: Having 1-2 years of experience in IT, particularly in network support, systems administration, or security roles, will be advantageous.
While these prerequisites help, they are not strict requirements. Enthusiasm and a willingness to learn can also pave the way for your success in this course. If you are passionate about cybersecurity and ethical hacking, our comprehensive training will equip you with the skills and knowledge you need.
RoadMaps

Target Audience for Certified Ethical Hacker v13 (AI) CEH
Certified Ethical Hacker v13 (CEH) offers advanced training in ethical hacking powered by AI capabilities, targeting IT professionals aiming to enhance their cybersecurity skills.
- Ethical Hackers
- Penetration Testers
- Network Security Specialists
- Information Security Analysts
- Cybersecurity Consultants
- IT Auditors
- Site Administrators
- System Administrators
- IT Managers
- Aspiring Cybersecurity Professionals
Learning Objectives - What you will Learn in this Certified Ethical Hacker v13 (AI) CEH?
Certified Ethical Hacker (CEH) v13 Course Introduction
The Certified Ethical Hacker (CEH) v13 course equips students with the essential skills to identify, counter, and prevent cyber threats using the latest AI-powered techniques and tools. The training encompasses a wide array of security domains, from social engineering to cloud computing.
Learning Objectives and Outcomes
- Introduction to Ethical Hacking: Understand the fundamentals of ethical hacking, information security controls, relevant laws, and standard procedures.
- Footprinting and Reconnaissance: Learn techniques and tools for gathering information during the pre-attack phase.
- Scanning Networks: Master network scanning techniques and countermeasures.
- Enumeration: Discover various techniques including BGP and NFS exploits, and identify countermeasures.
- Vulnerability Analysis: Identify security loopholes and learn about different vulnerability assessment tools and types.
- System Hacking: Explore methodologies like steganography and steganalysis for identifying system and network vulnerabilities.
- Malware Threats: Understand different types of malware, procedures for malware analysis, and countermeasures.
- Social Engineering: Learn techniques for identifying theft attempts and auditing human-level vulnerabilities.
- **Denial-of-Service (DoS